A look at Its new guidelines for secure remote access
Lila Kee is Chief Product Officer at GlobalSign (http://www.globalsign.com), an identity services provider and certificate authority since 1996, and an NAESB-Authorized Certificate Authority (ACA) to the electric utility industry. Ms. Kee also serves as a participant in NIST-NCCoE Energy Sector Identity and Access Management Use Case Consortium, and member of the executive board for NAESB’s Wholesale Electric Quadrant.
Beyond death and taxes, there's another certainty these days - attempts at cybercrime in the energy sector.

Some 41 percent of the cyber incidents that occurred in fiscal year 2012 across all critical infrastructure sectors occurred in the energy sector, particularly electricity.1 From physical attacks on sub-stations,2 to malware-based attacks aimed at industrial control systems,3 threats against the electric grid have increased in frequency and level of sophistication. At the same time utilities increasingly are being asked to bring services online for external customers, partners and regulators, while adjusting their longstanding attitudes about the need to provide more secure remote access to resources.
As a result, several utility regulatory bodies have upped the ante with initiatives tailored to help secure one of the most significant points of exposure - remote access to the electric power grid, whether by employees, partners or customers.
The most notable of these efforts comes from the North American Energy Reliability Corporation (NERC), with the realization of Version 5 of its Critical Infrastructure Protection (CIP) standard, which goes into effect on April 1, 2016.
But don't dare treat this deadline as just one more April Fool's Day joke.
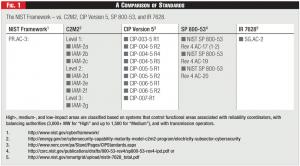 Figure 1 - A Comparison of Standards
Figure 1 - A Comparison of Standards
Grid providers should start early and allocate adequate resources to address updates to security management controls, training, network and physical systems, and information security as well as incident reporting, response and recovery planning. That said, they should also take heart that the changes they make will enable new business models, expanded capabilities and heightened peace of mind in an all-too-intrusion-driven age.
There's no question that the changes envisioned in CIP Version 5 are needed to meet modern threats to the grid. Digital systems now stand at the front-end of older operating technologies, which once had the advantage of being isolated from online threats. Internet-enabled devices now are everywhere, with as many as 50 billion people, processes, connections, and things projected to be in use by 2020.4 As the Internet of Everything (IoE) expands, each device offers the potential to gain access to a utility's computing resources.
In many ways, NERC's CIP Version 5 is doing for the utility industry what information security experts have called for industries across the board to do: to implement controls for identity and access management (IAM) for areas that either lack them entirely, or have only low-level protection.
Separate initiatives from the National Cybersecurity Center of Excellence (NCCoE), a part of the U.S. National Institute of Standards and Technology (NIST), and from the U.S. Department of Energy's Energy Sector Cybersecurity Framework program - an outgrowth of President Obama's Executive Order around CyberSecurity for Critical Infrastructure - also can play a part in readying the Bulk Electric System (BES) for the mandatory changes required by NERC's CIP Version 5.
Tightening the Security Perimeter
One area where the stricter controls of CIP Version 5 will enhance grid security is in the area of secure remote access, as addressed in NERC Standard CIP-005, Electronic Security Perimeter. As NERC explains, CIP-005 addresses how owners and operators of Bulk Electric Systems5 should "manage electronic access to BES Cyber Systems by specifying a controlled Electronic Security Perimeter in support of protecting BES Cyber Systems against compromise that could lead to misoperation or instability in the BES."
And CIP-005 marks just one of several NERC Standards, ranging from CIP-002 through CIP-009, where a set of cybersecurity standards is aimed collectively at the identification and protection of critical cyber assets to support reliable operation of the Bulk Electric System. Let's take a closer look at how CIP Version 5 updates strengthen CIP-005 in the area of Interactive Remote Access controls.
CIP Version 5 closes many of the security gaps around unauthorized access to those systems that weren't addressed in Version 3. Updates in Version 5 tackle vulnerabilities related to both internal and remote access in three important areas:
- Increasing asset coverage - avoiding pitfalls of the past, such as misclassification of assets at levels than don't align with their risk profile. In Version 5 remote access controls are explicitly specified for both high- and medium-impact BES system assets.
- Adding stricter controls around remote-access requirements for up-to-date patch levels on user computers and mobile devices.
- Delineating greater prescriptive measures to prove compliance, such as authenticators that could meet the multi-factor authentication requirement around interactive remote sessions.
Version 5 expands upon the risk-based approach to classifying assets that existed in previous versions. That helps determine the appropriate assurance level assigned to any given system. As one would expect, the stakes have increased around the area of identity, access, and authorization to medium- and high-impact systems.
Meeting the new requirements of Version 5 should not be difficult for early participants who implemented CIP Version 3. One participant reports that about 70 percent were still applicable - but had to revise their documentation to meet the new requirements or make other modifications.
Risk-Based Assessments
Assessing the potential loss associated with a system compromise in the context of grid reliability - in either economic and safety terms - provides the key to determining the level of security needed. In NERC's CIP Version 5, a risk-based approach is used to first classify assets, and after that, to apply the security requirements.
Three key Version-5 guidelines for bulk electric cyber systems that affect all medium and high-impact systems include the following:
- Part 1.3: Requiring inbound and outbound access permissions, including the reason for granting access, and denying all other access by default.
- Part 2.2: Requiring all interactive remote access sessions to utilize encryption that terminates at an intermediate system.
- Part 2.3: Requiring multi-factor authentication for all Interactive Remote Access sessions.
Use Case Examples
Meanwhile, other energy industry groups are working to boost security for remote access in the spirit of what the new NERC CIP Version 5 requirements are working to accomplish. The topic is vital since so many energy companies are looking to various online offerings to enable new revenue streams, provide better customer service, and reduce costs associated with vendor supply chain management. Such aims go above and beyond the traditional requirements for secure remote access to grid systems by operators.
Both the National Cybersecurity Center of Excellence (managed by NIST) and its Energy Sector Identity and Access Management User Case consortium are tackling some of these very same use cases concerning Identity and Access Management (IdAM), including remote access, that are addressed in CIP Version 5. The NCCoE's corresponding reference design provides a practical guide that can help address CIP Version 5 updates, but more importantly, improve grid security.
Rather than issue prescriptive requirements, the NCCoE has spent several years in sharing industry best practices and making recommendations around commericial off-the-shelf products and services. Indeed a major component of the NCCoE's IdAM initiative for the energy use case has been the definition of a framework that incorporates real-world applicabiilty to standards governing the electricity sector, such as NERC CIP Version 3 and Version 5.
By facilitating a public-private sector initiative around the idea of developing an IdAM reference architecture, NCCoE is assisting grid system owners on how they might address cybersecurity threats by implementing identity and access controls.
For example, the NCCoE Energy IdaM Use Case consortium published an illustrative scenario of typical examples of remote access at an electric substation to show the key requirements that reflect the expectations of doing business online today - whether internally, with partners, or with customers. Among these expectations are the following:
- Mobile Devices. Acknowledged as legitimate methods to access secure networks - which was not the reigning philosophy 3-5 years ago.
- IP-Connected SCADA. Such systems (for "supervisory control and data acquisition") are today presumed to be onboard - both for convenience and for a greater level of control around remote access
- Simplified End-use. A more streamlined experience, through security that isn't overly burdensome
- Single-Identity Credentials. For physical, operational, and IT access.
- Stronger Authentication Requirements. For authorized personnel access to medium- and high-risk areas. For example, replacing single-factor, password-based authentication with multi-factor credentials including digital certificates based on Public Key Infrastructure (PKI) can help grid operators to sustain much-needed productivity and reliability with the enhanced security their critical operations require.
- Federated Identities Support. To allow utilities, their partners, and customers to bring along their own identities, and to enable Single Sign-on (SSO) implementations from their own network, eradicating the need for yet another password.
- Stronger Device Authentication. Important, since the device a user is attempting access from is often tied to a mobile device management platform.
- Rules-Based Authorization. Fine-grained requirements to govern authorization for access, activity, and time frame of access.
- Stronger Audit Trails.
- Encrypted Sessions. To protect the systems, data, and privacy of the two organizations at each end.
Access Beyond Employees
While the NCCoE use case focuses on remote access for employees, utilities increasingly face challenges on how to bring online services to external customers, partners, and regulators. In many ways, the reference architecture guidelines seen in the NCCoE use case studies will apply also to these situations.
Here the key to cost-effective, scalable, and affordable implementations will come from authentication that employs a variety of methods, ranging from social log-ons to PKI-based digital certificates. A wide variety of assurance levels will be needed to determine the level of identity verification, the type of credential used, and burden on the end user - all associated with the risk of the resource being accessed. One business-to-consumer use case taking off in Europe is seen in Finland, where utility companies are mandated by regulations set by the Energy Authority to allow consumers to review their consumption data gathered by smart meters.
Nevertheless, utility companies must remain mindful that the IdAM solutions that work for employees and business partners might not be suited for external users, especially consumers. Utilities should consider the following business benefits when selecting an IdAM solution:
- Easy consumer self-registration and management.
- Efficient deployment of strong consumer authentication alternatives.
- Low threshold to use secure services.
- Support for mobile device access.
- Maximum compatibility and reduced development time, through support for standards such as SAML 2.0, OpenID, OAuth 2.0, and WS-Federation, as well as RESTFUL APIs for custom integration.
A Self-Assessment Checklist
While planning for updates to implement CIP Version 5, utilities should also use the guidance on the NIST Cybersecurity Framework as issued in January 2015 by the U.S. Department of Energy. DOE's guidance takes the original NIST Cybersecurity Framework (published Feb. 12, 2014, for use by all critical infrastructure sectors) and focuses it specifically on the energy sector. It also factors in energy-specific cybersecurity tools and processes, such as NERC CIP and the DOE's Cybersecurity Capability Maturity Model (C2M2).
Think of Section 5 of the C2M2 as a self-assessment checklist ahead - made available ahead of the NERC CIP version 5 switchover. With it, energy owners and operators can gauge where they stand against the Cybersecurity Framework. The good news is that energy owners and operators do not need to run parallel cybersecurity programs in order to communicate to key stakeholders such as executives, regulators and CISOs which NIST framework maturity tier that they operate within.
Endnotes
1. U.S. Department of Homeland Security (2013) "Incident Response Activity," ICS-CERT Monitor. April-June. Also cited here.
2. On April 16, 2013 there was a sniper attack on electrical transformers owned and operated by PG&E Corporation causing millions of dollars of damages.
3. Duqu is a collection of malware related to the Stuxnet worm gear at attacking Industrial Control systems.
4. "How Many Internet Connections Are There in the World?," Cisco blog, July 29, 2013.
5. NERC defines Bulk Electric Systems as "Transmission Elements operated at 100 kV or higher and Real Power and Reactive Power resources connected at 100 kV or higher."
Lead image © Can Stock Photo Inc. / kran77


